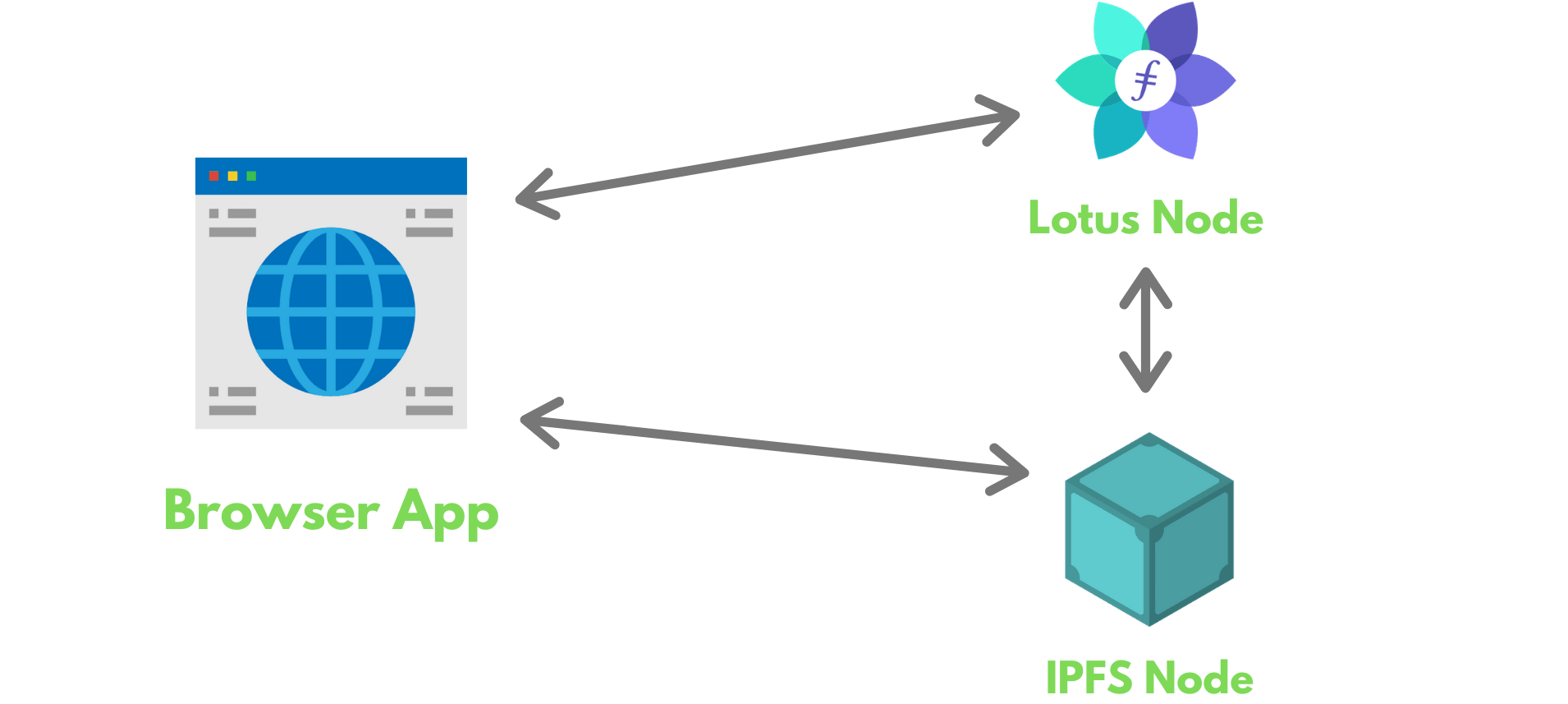
Step 2:
IPFS and Arwaeve supported currently, more to come!
NuCypher provides a proxy re-encryption network for additional security.
Arweave
Upload or download model
with Arweave!
Please select your arweave keyfile
Upload a file to arweave
Upload
Search for a transaction hash on arweave
Model Utility
Combine Models!
Please select your model files

A proxy re-encryption network to empower privacy in decentralized systems!
NuCypher
1
Data owner, Alice, grants access to her encrypted data to anyone she wants by creating a policy and uploading it to the network
2
Collaborator or other entity can encrypt data on Alice's behalf using public key. The resulted encrypted data can then be uploaded to IPFs or any other storage layer.
3
A group of Ursulas (nodes of the NuCypher network) receive the access policy and re-encrypt data in exchange for rewards. (The use of proxy re-encryption guarantees that Ursulas, and the storage layer never have access to Alice's plaintext data.)
4
Data recipient, Bob, sends an access request to the NuCypher network. If Bob was granted an access policy by Alice, the data is re-encrypted for his public key, and he can subsequently decrypt it with his private key.
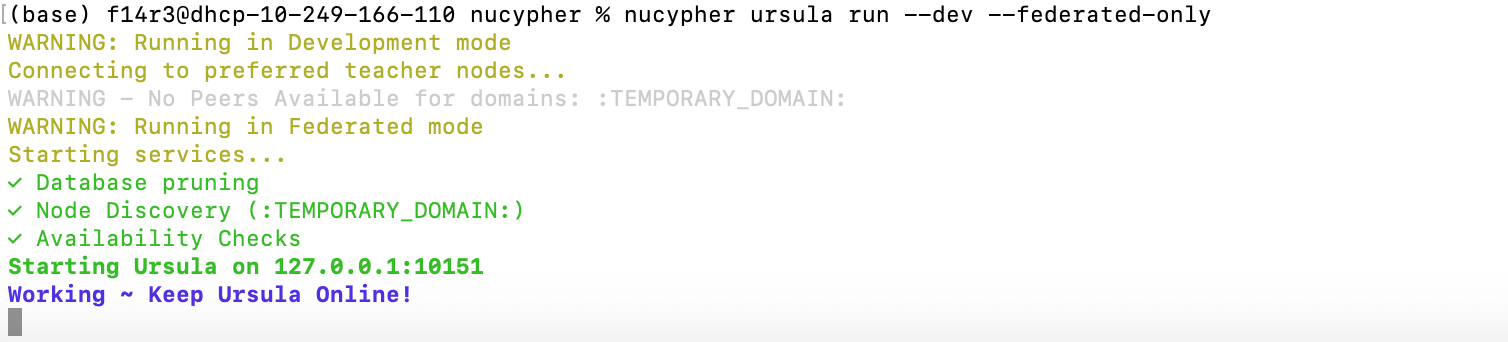
Run ursula:
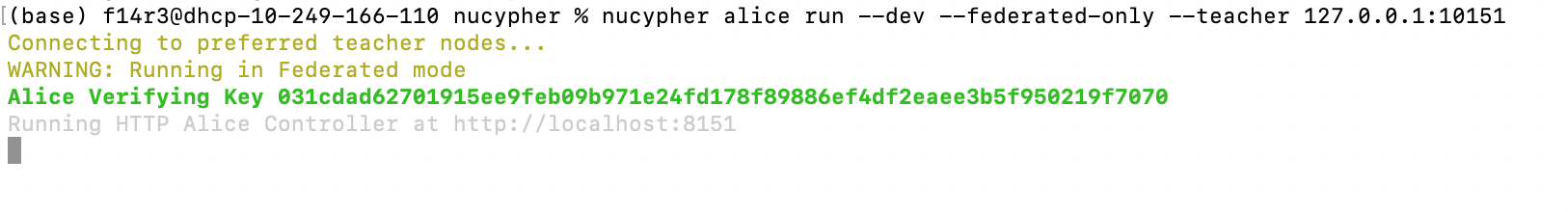
Alice run:
 Create a label (derive_policy_encrypting_key):
Create a label (derive_policy_encrypting_key):
This endpoint controls the Alice.get_policy_pubkey_from_label method.
URL: /derive_policy_encrypting_key/<\label\> Method: POST
Returns: a hex-encoded policy_encrypting_key
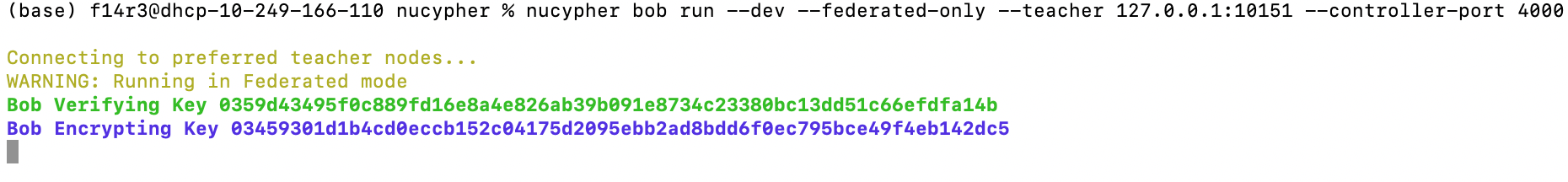
Bob run:
 This endpoint controls the Alice.grant method.
This endpoint controls the Alice.grant method.
URL: /grant HTTP Method: PUT
Start Enrico:
Encrypt the message:
This endpoint controls the Enrico.encrypt_message method.
URL: /encrypt_message HTTP Method: POST
Message Retrieve:
This endpoint controls the Bob.retrieve method.
URL: /retrieve HTTP Method: POST
nucypher ursula run --dev --federated-only

Alice run:
nucypher alice run --dev --federated-only --teacher 127.0.0.1:10151
 Create a label (derive_policy_encrypting_key):
Create a label (derive_policy_encrypting_key):This endpoint controls the Alice.get_policy_pubkey_from_label method.
URL: /derive_policy_encrypting_key/<\label\> Method: POST
Returns: a hex-encoded policy_encrypting_key
Bob run:
nucypher bob run --dev --federated-only --teacher 127.0.0.1:10151 --controller-port 4000
 This endpoint controls the Alice.grant method.
This endpoint controls the Alice.grant method.URL: /grant HTTP Method: PUT
Start Enrico:
nucypher enrico run --policy-encrypting-key $key$ --http-port 5000
Encrypt the message:This endpoint controls the Enrico.encrypt_message method.
URL: /encrypt_message HTTP Method: POST
Message Retrieve:
This endpoint controls the Bob.retrieve method.
URL: /retrieve HTTP Method: POST
Step 3: and Get Rewards!
Tezos! Till Everyone Zap One Score!
Technology Employed